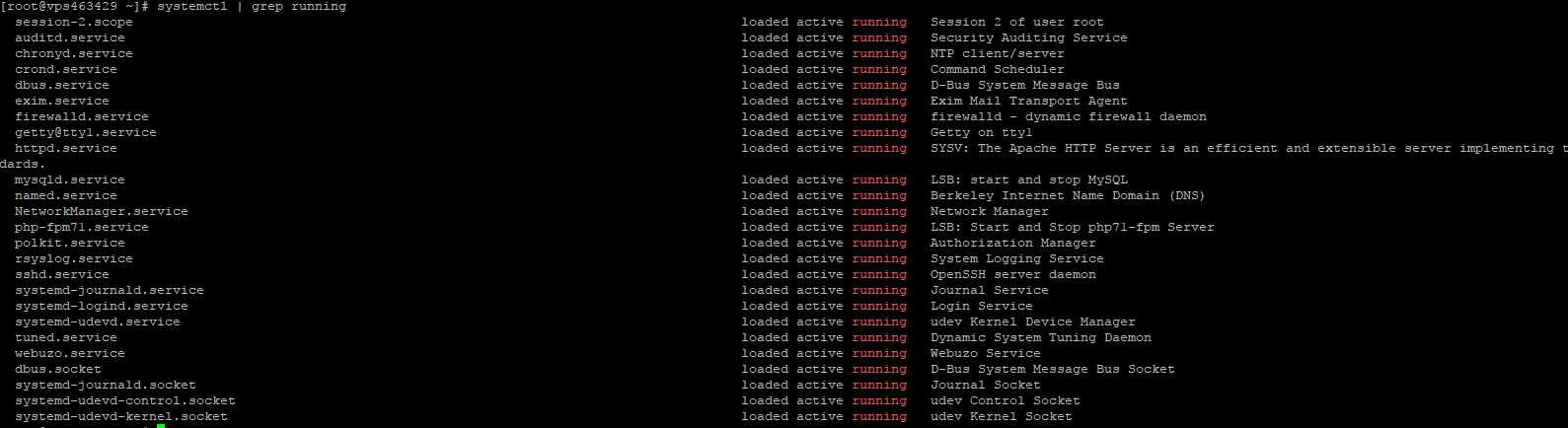
Nu e foarte clar ce înţeleg aia de la suport prin “porturi deschise/inchise”. Vezi sa nu ai portul 80 blocat din firewall, incearca in prima faza de opresti complet firewall-ul: systemctl stop iptables
Mi-au răspuns din nou, am trimis datele de logare să verifice ei:
I have checked and the data is on the VPS under the /home/ directory, it also looks like the services are running but there is something on the VPS itself which is blocking the ports. It is possible that firewall rules such as IPtables were lost on the restart.
Unfortunately, we are limited in the support that we can provide for the software side of the VPS as our network and host level are working correctly.
@serghei, am făcut ceea ce mi-ai spus și i-am dat și un restart serverului. Nu s-a schimbat nimic, tot nu merge.
@Opencart_Romania, am folosit comanda:
- systemctl restart httpd
Nu mi-a dat nici o eroare, de asemenea am verificat:
Vezi ca daca dai reboot dupa ce opresti firewall-ul, firewall-ul se va activa din nou. De fapt ce anume nu merge? Ce eroare da in browser? Poti sa postezi o captura de ecran?
Am refăcut acum ce ai spus și la fel, nimic schimbat. Nu înțeleg de ce serviciul nu a revenit la normal automat.
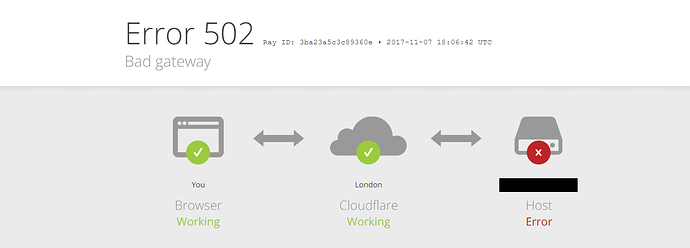
Dacă vreau să intru pe IP la fel, pagină albă. Spune că nu merge.
Prostia asta de eroare mai mult incurcă decât ajută  Nu sunt foarte sigur cum functioneaza Cloudflare, e un soi de reverse proxy in faţa web serverului?
Nu sunt foarte sigur cum functioneaza Cloudflare, e un soi de reverse proxy in faţa web serverului?
Ia sa vedem ce ai tu acolo, baga comenzile astea:
netstat -lnpt
si
iptables -L -v -n
Ah, si mai e ceva, vezi sa nu-şi bage coada SELinux, incearca sa-l dezactivezi temporar: setenforce 0
EDIT: mai sus scrii ca atunci cand bagi ip, îţi apare pagina albă. Vezi că e o diferenţă între o pagină albă şi eroare de la Cloudflare, fii mai precis.
[root@vps463429 ~]# netstat -lnpt
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 819/exim
tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN 819/exim
tcp 0 0 0.0.0.0:2002 0.0.0.0:* LISTEN 877/nginx: master p
tcp 0 0 0.0.0.0:2003 0.0.0.0:* LISTEN 877/nginx: master p
tcp 0 0 0.0.0.0:2004 0.0.0.0:* LISTEN 877/nginx: master p
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN 951/pure-ftpd (SERV
tcp 0 0 0.0.0.0:2005 0.0.0.0:* LISTEN 877/nginx: master p
tcp 0 0 193.70.112.77:53 0.0.0.0:* LISTEN 828/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 828/named
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 922/sshd
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 828/named
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 819/exim
tcp 0 0 127.0.0.1:8999 0.0.0.0:* LISTEN 1127/perl
tcp6 0 0 :::587 :::* LISTEN 819/exim
tcp6 0 0 :::80 :::* LISTEN 1527/httpd
tcp6 0 0 :::465 :::* LISTEN 819/exim
tcp6 0 0 :::21 :::* LISTEN 951/pure-ftpd (SERV
tcp6 0 0 :::22 :::* LISTEN 922/sshd
tcp6 0 0 :::25 :::* LISTEN 819/exim
tcp6 0 0 :::443 :::* LISTEN 1527/httpd
tcp6 0 0 :::3306 :::* LISTEN 1319/mysqld
[root@vps463429 ~]# iptables -L -v -n
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
624 57125 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
9 1090 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
123 6223 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 1127 packets, 107K bytes)
pkts bytes target prot opt in out source destination
1127 107K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD_IN_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_OUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public all -- * eth0 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_direct (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDI_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDO_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
591 22071 IN_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain INPUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public (2 references)
pkts bytes target prot opt in out source destination
591 22071 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
455 15108 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain IN_public_allow (1 references)
pkts bytes target prot opt in out source destination
13 740 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW
Chain IN_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
[root@vps463429 ~]#
E mai bine decât să-ți las un print.
[root@vps463429 ~]# setenforce 0
setenforce: SELinux is disabled
[root@vps463429 ~]#
Nu înțeleg cum suspendă ei un serviciul, ți-l pune în shutdown sau? După plată, s-a activat imediat serviciul și îmi arăta asta:
Nu prea arata bine. Firewall-ul e tot activat, iar httpd “ascultă” asculta pe portul 80 doar pe ipv6, pe ipv4 “tace”. Ia vezi daca e ceva suspect prin /var/log/httpd/error_log (vreun warning sau ceva de genul). Si mi-e clar, folosesti pana la urma nginx sau apache?
Foloseste Apache
Mie imi da asa:
[serghei@t520 ~]$ telnet 193.70.112.77 80
Trying 193.70.112.77...
telnet: connect to address 193.70.112.77: No route to host
Asta inseamna ori ca ruta spre ip este incorecta sau ca ip-ul e gresit ori firewall-ul este activ si rejecteaza portul 80.
Asta mi-au răspuns și cei de la OVH. Cum aș putea rezolva?
Pai ti-am zis sa opresti firewall-ul, si pare tot pornit.
Am trimis această comandă via SSH.
![]()
Salutare!
Vezi ca am scris mai sus…
IP-ul este pe o virtuala… problema este de la resol.conf-ul care ti-a fost rescris la suspendare
nameserver 127.0.0.1
nameserver ip_ul_tau
search ovh.net
Deasemeni verifica daca FQDN este corect setat
hostname
Asta e problema, dupa asta faci un systemctrl network reload
Spor
ps: deasemeni vezi ca ai posibilitatea de configura / activa / dezactiva firewall-ul din panel-ul ovh.
Si dupa ce ai trimis comanda asta ai rulat iptables -L -v -n ca sa fii sigur ca intr-adevar s-a oprit? Ia baga de curiozitate o regula:
iptables -I INPUT -p tcp --dport 80 -j ACCEPT
Am intrat cu WinSCP în acest fișier și am așa:
# Generated by NetworkManager
search openstacklocal ovh.net
nameserver 213.186.33.99
Nu, am făcut-o acum, am adăugat și cealaltă comandă.
[root@vps463429 ~]# iptables -L -v -n
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
624 57125 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
9 1090 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
123 6223 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 1127 packets, 107K bytes)
pkts bytes target prot opt in out source destination
1127 107K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD_IN_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_OUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public all -- * eth0 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_direct (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDI_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDO_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
591 22071 IN_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain INPUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public (2 references)
pkts bytes target prot opt in out source destination
591 22071 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
591 22071 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
455 15108 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain IN_public_allow (1 references)
pkts bytes target prot opt in out source destination
13 740 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW
Chain IN_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
[root@vps463429 ~]# ^C
[root@vps463429 ~]# setenforce 0
setenforce: SELinux is disabled
[root@vps463429 ~]# ^C
[root@vps463429 ~]# systemctl stop iptables
[root@vps463429 ~]# systemctl stop iptables
[root@vps463429 ~]# iptables -L -v -n
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2269 212K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
9 1090 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
1154 44231 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
1154 44231 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
1154 44231 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
315 15911 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 2942 packets, 1391K bytes)
pkts bytes target prot opt in out source destination
2942 1391K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD_IN_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_OUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public all -- * eth0 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_direct (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDI_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public (2 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDO_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
1154 44231 IN_public all -- eth0 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain INPUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public (2 references)
pkts bytes target prot opt in out source destination
1154 44231 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
1154 44231 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
1154 44231 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
822 27380 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain IN_public_allow (1 references)
pkts bytes target prot opt in out source destination
17 940 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW
Chain IN_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
[root@vps463429 ~]# iptables -I INPUT -p tcp --dport 80 -j ACCEPT
[root@vps463429 ~]#
Alta viata, ia incearca acum sa intri pe ip.
Salutare!
Bun asa!
Iptables incapatinat!
Spor!
@serghei, da, merge totul acum. Mulțumesc mult, apreciez ajutorul gratuit! 
Să te angajeze ăștia de la OVH că mi-au dat niște răspunsuri în 3 zile de te doare capul…
Mulțumesc pentru timpul vostru acordat! 
Stai ca n-ai terminat  Regula aia va disparea dupa primul reboot, va trebui s-o faci persistenta.
Regula aia va disparea dupa primul reboot, va trebui s-o faci persistenta.